Best Practices for Securing API Endpoints
With the fast development of technology in the digital world, APIs (Application Programming Interface) have ensured to change the IT world for business owners, making it much easier than in traditional times. From sharing photos and live map locations to shopping online or booking a hotel room or a flight, everything is done within a few seconds with the help of the API platform. It is an innovative approach to speed up the pace of the business flow. Even though APIs have been a part of our daily lifestyle, it is essential to take care of API endpoint advanced security.
Why Is API Security Important?
API security is important because it prevents any malicious or fraudulent activities when the APIs are connected to the server. As API is the main key in programming web-based interactions, it becomes dangerous to leave the API vulnerable to data breaches. The API's advanced security is to protect the integrity of the API. When business users use APIs to connect to servers to transfer data, they expose the data to hackers. Failing to manage security can lead to major business loss, compliance issues, a surge in infrastructure bills, and reputation loss. So, it is very crucial to ensure that the end-to-end api management is taken care of.
How Are API Endpoints Secured?
There are easy ways to ensure that endpoint security management is handled with care. Here are some significant ways of securing the API endpoints are:
Prioritizing the safety and security of the business
Authorizing the users who use the API key
Inculcating the practice of using HTTP
Identifying the inventory of all APIs and
Using a one-time password with strong encryption
Making use of rate-limiting to block DoS attacks and open access to hackers
Encrypting the traffic that uses TLS (Transport Layer Security) with sensitive data
Limiting unnecessary traffic
Deleting information that is restricted to certain users
Considering the client requests by blocking any unnecessary geographies
Using XDR systems for robust protection of APIs
Best Practices For Securing API Endpoints
Although it can be challenging to find the best way and the right application to ensure that your API endpoint is secured, here are a few best practices you should follow.
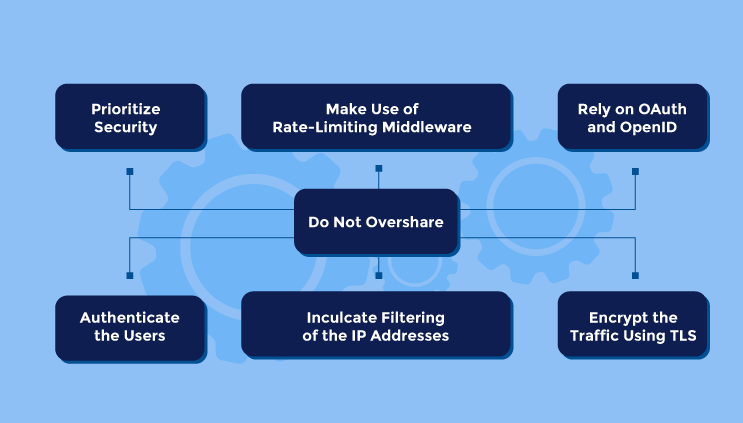
Prioritize Security
When you ignore securing the API endpoint, you put the entire business at risk due to the chances of data breaches. Whether it is a daily lifestyle chore or for business requirements, it is better to rely on experts to make sure the API is well-secured.
Authenticate the Users
Whenever an opposite party communicates, it is important to instill authentication in the process to ensure that the identity of who is communicating is verified and exactly who they claim to be. The best way to authenticate the users is by using the basic authentication, HTTP. It requires the user to provide their user ID and password.
An API key is another way to authenticate, where the user would need a unique identifier for each API and the known api gateway.
Encrypt the Traffic Using TLS
There should be nothing left in the air for internal or external communications. It is essential to make everything crisp and clear by converting the information into code. This prevents hackers from decoding sensitive data and information. All information that is communicated should be coded and passed through the TLS (one-way TLS or two-way TLS). Mostly, many business organizations do not plan on encrypting their TLS because they might have non-sensitive data. However, organizations that exchange highly sensitive data on a routine basis must always ensure to encrypt the Transport Layer Security.
TLS protects information like login credentials, credit card details, banking information, social security number, api documentation, and health information. When you encrypt the TLS, it ensures to conceal all the sensitive data is from any maliciousness or misuse.
Rely on OAuth and OpenID
Delegating the responsibility of APIs should be carefully done. You should hand over the APIs to a third-party Identity Provider (IdP), who manages the authentications. OAuth 2 is a great mechanism that remembers thousands of passwords for you. Rather than creating a new password on each website, you can easily connect from another provider’s credentials.
The token provided by the third-party server protects you from disclosing the given credentials. The OAuth adds authentication and also allows you to add another layer of identity.
Make Use of Rate-Limiting Middleware
If the API is not used by millions of people every second, the best thing to do is apply limits on the number of API endpoint calls the client can make in a limited period on the window. Applying rate-limiting eliminates the bots making their way in and making your API consume system resources. It is only a couple of minutes of work to set up a rate limit for extra security and ensure that you stay relaxed and comfortable.
Inculcate Filtering of the IP Addresses
If it is a B2B business service, where the APIs are used by stakeholders from different locations, you should consider adding another layer of API endpoint security to restrict the IP addresses that can easily access your API. This way, every IP address of the new clients and locations is thoroughly checked to ensure tight and prominent security for your api manager and API endpoint.
Do Not Overshare
Yes, it is essential in business to share the bare minimum, especially when there are several error messages during communication. However, it is imperative not to display all the information that can be easily accessed by anybody using your API and share only the highly required ones. It prevents you from exposing the data to unnecessary viewers. You should restrict access to your resources and separate the access to different users by hiding crucial information.
Summing It Up
APIs have become the preferred method for modern business applications in today’s world. So, with the developing technology, it is crucial to maintain the safety and security of oneself and the other parties. Though hacking and misusing information has been very common thing for decades, the development in technology has never stepped back from inventing ways to prevent it.
Whenever you combine the right technology that offers accurate resources required to enhance your business, you should deliberately indulge in the security process first to ensure you do not face major problems in the future. If you find difficulty finding the right API platform for developing all these steps for the security, you can trust Unified.cc application developed and launched by 500apps. It ensures endpoint security management stays intact while maintaining regulatory compliance. To find more details about the Unified API platform, visit 500apps now.
Know Why Unified.cc is Best for Unified API Platform?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
