What Is API Security Importance
APIs or Application Programming Interfaces are vital components of digital transformation initiatives. They are becoming increasingly vital as integration and interconnectedness grow more important. Thus, protecting such APIs is a major concern. APIs are constantly rising attack surface that is often disregarded by developers and application security administrators.
What is API Security?
An application programming interface (API) is a method for one piece of software to communicate with another. Most current online apps rely on APIs to function, and APIs increase the risk of attack by enabling third-party access to them. API security is the practice of defending APIs against assaults. Thus, API advanced security is an important aspect of online application security.
API Security Importance with Some Examples
APIs are the foundation of today's digital ecosystems. They are firmly embedded in software systems and constitute a key driving factor in the effective execution of applications. APIs are also used by standard client-server applications to exchange data.
Furthermore, third-party API consumption is a common method of integrating APIs with existing systems using api manager. APIs are crucial stakeholders in microservices, the most innovative and widely utilized application architectural paradigm these days, in addition to traditional client-server or third-party interactions.
As a result, protecting APIs to limit their vulnerability and contributing to a transparent API economy becomes a duty that organizations simply cannot avoid.
API Security Examples
Here are some examples where API security is key.
Inventorying APIs
As digital transformation projects hasten the creation of new APIs, you must examine new APIs for suitable security measures. An AI engine will uncover APIs that were previously unknown to security practitioners by examining API traffic records. This degree of API discovery guarantees that rogue API blind spots are minimized. When new APIs are identified in this manner, they must be subjected to an API security checklist.
API Threat Identification
You can detect threats in real-time with API security. An api gateway, a WAF, or an agent implementing a set of validation criteria is used for real-time threat detection. Nonetheless, there is a limit to how many layers of real-time security may be implemented sequentially before latency suffers.
Out-of-band API traffic analysis should be delegated to a specialized AI engine that is not connected to the API traffic stream. You can capture API traffic metadata from this AI engine to develop ML models for each API and track error rates, API sequences, and API grouping across tokens, API keys, IP addresses, cookies, and so on.
API Security Best Practices
If enterprises plan to offer their APIs publicly, they must follow certain fundamental security best practices and use well-established security measures.
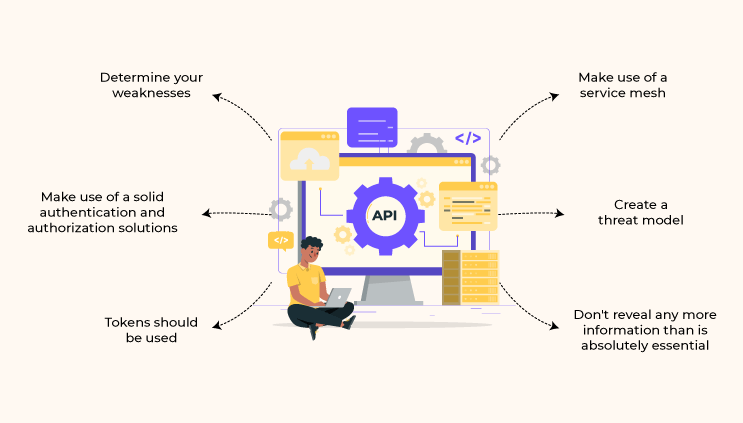
Determine Your Weaknesses
Knowing which stages of the API lifecycle are unsafe is the only way to safeguard APIs successfully. This may not be that easy to do, especially as the organization's usage of APIs grows. APIs must be regarded as software artifacts on their own and must follow a complete lifespan, including maintenance and retirement. It is essential to evaluate the entire API lifecycle in end-to-end api management.
Make Use of Solid Authentication and Authorization Solutions
Many publicly available APIs suffer from non-existent or poor authorization and authentication. Hackers can easily attack your APIs when you do not enforce authentication or when an authentication factor is readily broken into. As APIs give access to an organization's databases, access to them is properly controlled. You must use solutions based on robust, established authentication and authorization technologies wherever possible.
Tokens Should Be Used
Token usage is a good API security practice in general. Tokens granted to identities can be used by developers as a reasonably simple method to control access to services and establish trusted identities.
Make Use of a Service Mesh
Service mesh technology, like API gateways, adds another layer of control as it sends requests from one service to the other. A service mesh optimizes how all of these moving pieces interact, including the implementation of correct authentication, access control, and other security mechanisms. API administration is shifting to the service communication layer. Thus, solutions are accessible at the service mesh layer. If the APIs have easy deployment then the number of APIs grows, and automation and security become increasingly important.
Create a Threat Model
Threat modeling is a methodical way to identify and assess threats. Threat models are most effective when utilized as a preventative strategy, but they should also be viewed as a continuous cycle for analyzing, mitigating, and preventing application vulnerabilities in an automated yet regulated manner.
Don’t Reveal Any More Information than Is Essential
Some APIs give way too much information, whether it's the amount of unnecessary data returned by the API or information revealing far too much about the API endpoint. This usually happens when an API delegates the responsibility of filtering data to the user interface rather than the endpoint. You must ensure that APIs only return the information required for employees to perform their job. Furthermore, at the API level, you can impose data access limits, monitor data, and obfuscate if the return contains confidential data.
Summing it up

APIs are often regarded as the best technique for developing contemporary apps, particularly for mobile and Internet of Things (IoT) devices. While the notion of bringing information into a program from an external source is not new, continuously developing app development methodologies and the push to innovate mean that some firms may not yet understand the possible hazards associated with making their APIs publicly available.
Businesses must integrate mechanisms to resist well-known API-targeting attacks such as cross-site scripting, injection, distributed denial-of-service, and others. Several of the best practices mentioned in this blog can also help build strong API security standards and maintain them proactively over time.
One such application you can use is Unified.cc, which allows you to access multiple apps using a single unified API, allowing you to spend less time separately integrating multiple applications and services. In other words, Unified.cc makes it simple to connect to many services and data sources, making it an excellent choice for developing large-scale applications, all while providing high security.
Know Why Unified.cc is Best for Unified API Platform?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
