Difference between API Security and Unified API Protection
API security is the process of securing APIs from unauthorized access. Unified API protection provides security for all APIs in an organization from a single platform. Both approaches aim to secure APIs from malicious activity, but unified API protection provides a more comprehensive approach that includes protection from unauthorized access, data leakage, and denial of service attacks. APIs, both internal and external, now form a significant portion of an organization's digital footprint. As more IT leaders recognize and acknowledge the magnitude of APIs' significance, it is evident that new ways are required to protect those APIs.
While many firms currently use the phrase API security to describe their products, these solutions frequently handle just a subset of the various functions required to prevent APIs from becoming a source of vulnerability that may be exploited as an attack vector. Thus, a new attitude, a new category, and a real end-to-end solution are required, and Unified API Protection fits the bill.
How Does API Security Work?
An API is a software interface that determines how various pieces of software communicate with one another. It governs the sorts of requests made between programs, how they are made, and the data formats that are utilized. APIs are utilized on websites and in the Internet of Things (IoT) applications. They often collect and process data, or they let the user enter information that is processed within the environment that houses the API.
The process of preventing or mitigating attacks on application programming interfaces (APIs) is referred to as API security. APIs serve as the foundation for mobile and online apps. As a result, it is vital to safeguard the sensitive data they transmit. Traditional means of identification such as passwords and usernames are being phased out in favor of security tokens and multi-factor authentication with advanced security. This is how API security functions.
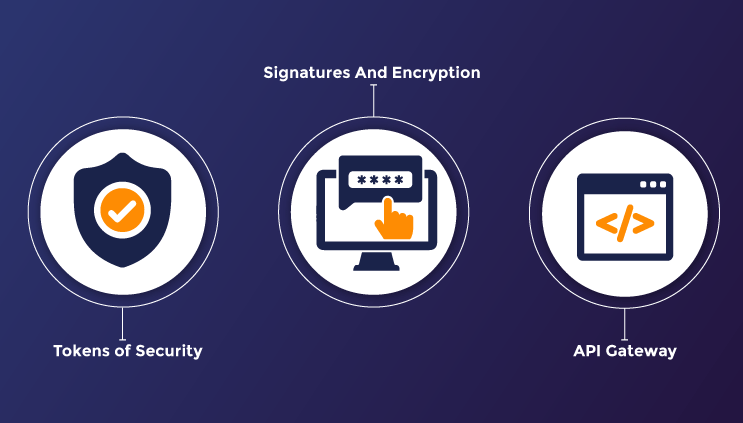
API security is largely accomplished through authorization and authentication. The first step in API security is authentication, which ensures that your application process has a secure identity that allows you to utilize an API. Authorization, on the other hand, is the following step that specifies the type of data that an authorized application has access to when connecting with an API. APIs are designed with additional security apart from secure authentication and authorization. Some of these features are given below:
Tokens of Security
A security token can be used instead of a password. It uses two-factor authentication to identify your login information. Therefore, before you may utilize any service or resource granted to an API, your tokens must be confirmed.
Signatures And Encryption
One method for advanced security is to use Transport Layer Security to implement data encryption and signatures. Transport Layer Security protects your internet connection and the data transmitted between you and a server. Without a signature that identifies the correct users, it is impossible to collect your data from a website.
API Gateway
An API gateway acts as a hub for all of your API traffic. A secure api gateway will authorize and authenticate your traffic while also allowing you to govern how you utilize your APIs. These capabilities detect API vulnerabilities by monitoring your network, API components, drivers, and operating system. They show your API's weak points and pinpoint regions where data breaches and security concerns are most likely to occur.
What is a Unified API Protection Solution
Unified API Protection differs from fragmented or incomplete API security services in that it is a technique meant to account for numerous forms of risk, enable autonomous detection, and, most significantly, provide native inline resolution without the usage of third parties. This api manager is supported by three functional pillars:
Discovery: An agentless API attack surface discovery tool gives security teams an attacker's perspective on their publicly accessible APIs and resources.
Detect: Unified API protection allows security teams to detect and track their APIs. They also enable security teams to analyze and remediate vulnerabilities to minimize code errors that can lead to data loss.
Defend: Using Unified API protection, security teams can protect their APIs from a wide range of automated API assaults. As it uses bots, unified API protection also enables teams to reduce bot-induced consequences like site outages, infrastructure cost overruns, incorrect sales analytics, and damage to brand image due to angry customers.
6 Key Differences Between API Security And Unified API Protection
Moving from discussing API security to unified API protection, there are several key differences to consider. Here are five important distinctions to keep in mind:
The distinction between API security and unified API protection is significant because APIs have emerged as the preferred development tool in response to program componentization, competitive business dynamics, and user expectations for seamless app experiences. APIs have provided enterprises of all sizes with velocity and a competitive edge, with research estimating that APIs account for 10-50 percent of enterprise revenue.
The very visible and well-defined nature of APIs has made them an appealing target for attackers. Unified API protection, on the other hand, accomplishes continuous API risk surface protection, allowing companies to realize the competitive and commercial benefits of ubiquitous api led connectivity in a safe and compliant manner.
API security does not provide a method for detecting and blocking sophisticated assaults that appear to be valid communications or transactions but are attempts to avoid and perpetrate fraud and theft. However, unified API protection allows for continuous real-time detection of API activity. It is capable of providing compliance and risk monitoring, as well as enhanced threat identification using artificial intelligence.
API security is not an end-to-end solution. Applying security just at the development stage causes an excessive load on the development team and ignores the reality that the API may be attacked. Applying security at the time of publishing without regard for the risk profile or potential coding problems is an invitation for attackers to exploit coding faults. In contrast, unified API protection is an end-to-end solution. This unified api control finds your subdomains, the cloud hosting service in use, any linked API endpoints, and any vulnerability to hacking.
They frequently employ a strategy of attempting to move more of the responsibility of security and compliance to development teams. These attempts to shift responsibility fall short, leaving the business vulnerable to unknown and unchecked security and compliance risks posed by "shadow" APIs and infrastructure. In unified API control, bots detect and avoid the most sophisticated automated API assaults, thus reducing dependency on development teams for security.
Unified APIs integrate with any network infrastructure element to produce an up-to-date catalog of all your APIs, giving you an inside-out perspective of your APIs. However, in API security, implementations and integration are frequently disregarded or handled as an afterthought.
How Can A Unified API Platform Address Security Issues?
Unified.cc by 500apps is the best-unified API Protection solution on the market. It is the best solution to handle all the drawbacks of API security and can introduce a unified API control to your business.
The application comprises complicated authentication methods, and access restrictions meant to prohibit unauthorized user access and protect APIs from unauthorized access. It also helps security teams remove unknown, unprotected, and untreated API risks. They accomplish continuous API risk surface protection, allowing their companies to realize the competitive and commercial benefits of ubiquitous API connection in a safe and compliant manner.
Summing It Up
Security teams adopting unified API Protection allow their companies to boost revenues, cut service delivery costs, and improve user experience across all API-enabled apps by blocking threats without impacting good traffic. They also alleviate the worry and expenses associated with unknown risks by eliminating previously unprotected and unchecked API security and compliance risks.
Unified.cc enhances visibility and protection while lowering costs, and decreasing fraud, data losses, non-compliance, and business misuse. To learn more about this application, visit the 500apps website today!
Know Why Unified.cc is Best for Unified API Platform?
Join the SaaS Revolution
-
All-in-One Suite of 50 apps
-
Unbelievable pricing - â¹999/user
-
24/5 Chat, Phone and Email Support
Infinity Suite
Tags
Email Finder Author Finder Email Validator Email List Email Hunter Email Checker Email Lookup Email Extractor Email Address Finder Email Scraper Find Emails CRM Software CRM Sales CRM CRM Software Enterprise CRM Software Cloud CRM Software Sales Enablement Workflow Automation Retail CRM Call Center CRM Real Estate CRM Sales Tool SDR Software Sales Engagement Platform Sales Qualified Leads Lead Management Tool Sales Tracking Sales Automation Outbound Sales Sales Prospecting Follow Up Leads Lead Management Call Center Software Call Center Software Outbound Call Center Auto Dialer Software Dialer Call Monitoring Automatic Call Distributor Answering Machine Detection Cloud Contact Center Software Virtual Call Center Call Management Time Tracking Time Tracking Employee Monitoring Time Tracker Time Tracking Software Timesheet Employee Time Clock Employee Tracking App Timekeeping Tracking App Time Clock App Applicant Tracking System ATS Applicant Tracking System Application Tracking System Applicant Software Recruiting Software ATS System Applicant Tracking Applicant Tracker Recruitment Software Candidate Relationship Management Systems Video Interviews Assessment Management Recruitment Software Video Interview Virtual Interview Coding Interview Interview Tool Online Assessment Employment Assessment Test Position Management Hiring App HRMS Software Human Resource Management HRMS Software HR Software Payroll Software Human Resource Software Employee Onboarding HRMS HR System Employee Management Document Management AI Writer Lead Enrichment AI Email Writer Sales Pitch Writer AI LinkedIn Outreach SEO Email writer Backlink Email Writer LinkedIn Chrome Extension Opening Line Writer Lead Generation Linkedin Search Prospect Lead Generation Sales Generation Data Enrichment CRM Integrations Technology Search Search with Email Integrations Website Search OKR Tool KPI OKR Task Management Performance Review Employee Performance Evaluation Employee Review Performance Management System OKR Goals MBO Email Notifications Learning Management System LMS Elearning Enterprise Learning Management Professional Development Employee Training Learning Management System Learning Platform Asynchronous Learning Training Management Knowledge Management Chatbot Chatbot AI Chatbot Customer Service Chatbot Online Chatbot Create Chatbot Messenger Chatbot Chatbot Software Website Chatbot Software Survey Bot Bot Builder Help Desk Software Ticketing Tool User Experience Help Desk Software Ticketing System Helpdesk Ticketing System Feedback Management Service Desk Software Support Ticketing Software Helpdesk Support Software Customer Service Ticketing System Live Chat Customer Service Software Live Chat Software Live Chat App Live Chat System Website Live Chat Live Chat Tool Web Chat Software Live Chat Support Software Customer Service Tool Live Chat Service Customer Feedback Customer Feedback Survey Customer Feedback Management Software Feedback Management Tool Customer Satisfaction Survey Software Customer Feedback Management System Client Feedback Software Survey Analysis Feedback Survey Software Feedback Management System User Feedback Software Customer Onboarding Customer Success Management Onboarding Process Workflows Customer Retention Customer Journey Onboarding Checklist User Segmentation Personalization Customized Templates Popup Builder API Platform End To End API Management Unified API Control REST API Management Web API Gateway API Documentation API Management API Integration API Development Unlimited Projects API Gateway Single Sign on Authentication Software Application Management Password Management SSO Configuration SSO Single Sign-On Access Management Easy Set-Up Single Login Secure Login App Builder App Builder Platform Low Code Application Platforms Low Code Development Build Your Own App Low Code App Software Drag And Drop Builder Custom Application Low Code Platform Low Code No Code Bespoke Software App Widgets Custom Widget File Picker Playground OAuth Keys File Manager Website Monitoring Reporting Web Application Monitoring Website Monitoring App Monitoring Performance Monitor App Baseline Analysis Location Insights Alerting System Reporting Wireframe Tool Design UI UX Project Management Mock Designer Wireframe Designer Website Mockup UI Prototyping Image Library Project Management Real-Time Updates Design UI UX Website Builder Website Builder Webpage Builder Website Creator Landing Page Creator Website Maker Blog Builder Ecommerce Website Builder Website Analytics Website Development Landing Page Builder Email Marketing Email Marketing Software Bulk Email Sender Automated Email Email Campaign Systems Email Automation Software Autoresponders Email Blast Service Email Marketing Email Marketing Automation Drip Campaigns Social Media Management Instagram Post Scheduler Social Media Analytics Social Media Management Social Media Planner Social Media Calendar Social Media Scheduling Social Media Listening Social Media Monitoring Social Listening SEO Tool Keyword Tool Link Building SEO Optimizer Website Audit On-Page SEO Broken Link Checker Rank Tracker Website Grader SEO Competitor Analysis Website Recording Website Analytics Click Tracking Usability Testing Website Monitoring Mouse Tracking Visitor Recording Session Replay Conversion Funnels Website Recording Website Visitor Tracker Website Personalization Lead Generation Tool Popup Maker Lead Generation Software Popup Builder Website Personalization Software Lead Capture Software Popup Builder Lead Capture Tool Lead Generation App Website Personalization App Content Planner Content Planner AI Writer Social Media Content Planner Ai Content Writer Social Media Content Calendar Content Generator AI Blog Writer Content Marketing Software Social Media Calendar Social Media Planner Push Notification Push Notification Push Messages Push Notification Service Push Service Push Notification App Custom Notifications Mobile Push Notifications Push Notification For Website Push Notification Tool Push Notification Providers Image Personalization Email Marketing Template Countdown Clock Personalization Software Personalized Software Countdown Clock Countdown Timer In Email Personalization Tool Personalized Images Personalized Videos Conversational Chatbot PPC Management Keyword Research PPC Management PPC Marketing Keyword Finder Keyword Generator Shopping Ads Adwords Reports Keyword Research Tool Keyword Suggestion Tool Team Chat Team Chat Software Collaboration Software Team Collaboration Team Communication Online Collaboration Collaboration Tool Teamwork Collaboration Virtual Communication Team Collaboration Software Business Phone System Virtual Phone Numbers Virtual PBX Toll Free Numbers Business Phone System IVR PBX Small Business Phone System PBX System VoIP Phone Cloud Phone Video Conferencing Video Conferencing Video Call Recording Virtual Conferencing Software Virtual Meetings Virtual Meeting Platforms Virtual Conference Platforms Online Conference Platforms Video Calling Software Cloud Meetings Video Conferencing Software Email Provider Email Software Software For Emails Hosted Emails Email With Domain Custom Email Address Email Hosting Business Email Address Email Encrypted Custom Domain Email Project Management Software Project Management Task Management Project Planner Project Management Tool Task Management Software Project Planning Software Project Management App Task Management App Project Management System Project Management Software Form Builder Form Builder Survey Builder Order Forms Web Forms Form Maker Form Creator Form Designer Survey Maker Survey Creator Custom Form Appointment Scheduling Appointment Scheduling Software Appointment Scheduling System Meetings Scheduler Appointment Scheduling App Online Appointment Scheduling Online Scheduling App Appointment Scheduler Appointment Booking App Calendar Scheduler Online Scheduler Robotic Process Automation RPA Tools RPA RPA Automation Robotic Automation Software Data Scraper Web Scraper Robotic Automation Website Scraper Business Process Automation Robotic Process Automation Business Process Management Workflow Management Business Process Modelling Business Process Automation BPMN BPM Software BPM Tool Business Process Management Workflow Software Workflow Automation Business Process Mapping App Integration Workflow Software Workflow App Workflow Automation Process Automation Application Integration Data Integration Tool Workflow Management Software Data Integration Software Workflow Tool Marketing Automation Electronic Signature Signature Maker Digital Signature Software Digital Signature Pdf Signer Esign Online Signature Signature Creator Sign Documents Online Electronic Sign E Signature
